CyberSafe Chronicles
Newsletter Content
Tuque's Take on the News

Verizon insider data breach hits over 63,000 employees
Verizon Communications is warning that an insider data breach impacts almost half its workforce, exposing sensitive employee information.
Verizon is an American telecommunications and mass media company providing cable TV, telecommunications, and internet services to over 150 million subscribers across the U.S. A data breach notification shared with the Office of the Maine Attorney General reveals that a Verizon employee gained unauthorized access to a file containing sensitive employee information on September 21, 2023.
White Tuque’s Take: It is important to ensure that access is restricted on a need to know basis. Ensuring that there is tracking and monitoring of transaction logs around important data will help to identify where the breach occurred. As breaches become more common, it is becoming more important to verify notices and alerts as attackers will incorporate stolen data information to trick the recipients.
-Henry
We have subscription-based services that can help you find and auto-close vulnerabilities, monitor threats with managed detection and response (MDR), and more! Tell us more about your concerns at www.whitetuque.com/help.

Bank of America warns customers of data breach after vendor hack
Bank of America is warning customers of a data breach exposing their personal information after Infosys McCamish Systems (IMS), one of its service providers, was hacked last year.
Customer personally identifiable information (PII) exposed in the security breach includes the affected individuals’ names, addresses, social security numbers, dates of birth, and financial information, including account and credit card numbers, according to details shared with the Attorney General of Texas.
White Tuque’s Take: Understanding your third party’s cybersecurity posture of helps in understanding potential risks and vulnerabilities. This allows organizations to take proactive measures to mitigate these risks and ensure the security of their own systems and data. It also helps with the following:
- Protecting client data and IP
- Regulatory Compliance
- Reputatiion Management
- Contracts and Legal Protection
Does your organization perform due diligence before onboarding a vendor? Let us help you develop a strategy that works for your business to assess your vendor security! Tell us more about your business: www.whitetuque.com/help.

Clorox says cyberattack caused $49 million in expenses
Clorox has confirmed that a September 2023 cyberattack has so far cost the company $49 million in expenses related to the response to the incident.
On August 11th, Clorox suffered a cyberattack that caused significant disruption in the company’s operation, leading to lowered production and decreased availability of consumer products. In an earnings report filed with the SEC on Thursday, Clorox disclosed it incurred $49 million in expenses related to the cyberattack by the end of 2023. Read More…
White Tuque’s Take: The group that attacked in this incident specialize in social engineering attacks, where they target invidivuals within the organization to gain their trust and acquire critical information or credentials. Through this they breach the company’s networks and launch malicious attacks. It is important to create cybersecurity awareness and train employees on how to look out for phishing or social engineering attacks. Organizations often secure their infrastructure and do not invest in training their employees on security.
-Sree
Don’t think you have time for more training? Our approach is streamlined and refined to be relevant and tangibly useful for promoting best practices. Visit www.whitetuque.com/help to learn more.
Hear from Our Experts
Cyberattacks – The True Costs
It seems that every day brings a new headline detailing a major cyberattack resulting in significant operational issues, data corruption, or data loss. T-Mobile, The US State Department, and Microsoft all made headlines for major data breaches in the last month alone!
This is due to the advanced sophistication of threat actors, increased global connectivity (IoT), and an overall lack of understanding of what is needed to effectively manage cyber risks at the executive leadership level of most companies.
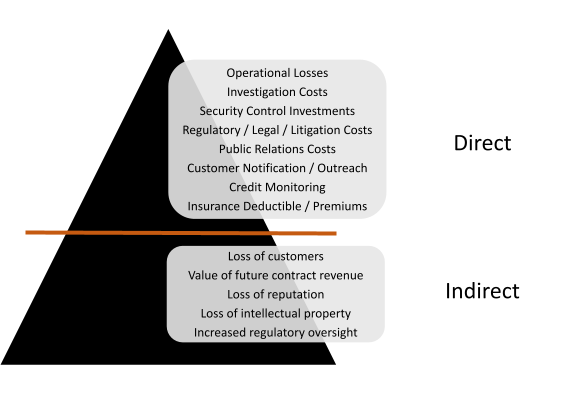
It is also important to note that these headlines only capture an extremely low percentage of cyberattacks globally, and they typically don’t tell the full story when it comes to the true losses the organization may incur.
To understand the complete view, we must consider both direct and indirect impacts when assessing the overall value at risk.

Types of Cyberattacks - Most Prevalent
- Malware: is any software designed to harm or exploit computer systems, often without the user’s knowledge or consent.
- Social Engineering: is the tactic of manipulating,
influencing, or deceiving a victim in order to gain control over a computer system, or to steal personal and
financial information. - Password Attack: is an unauthorized attempt to gain access to a computer system, network, or account by brute force until the correct one is found, often through automated or manual methods.
- Network Attack: is an attempt to gain unauthorized
access to an organization’s network, with the objective
of altering, destroying and stealing data or perform other malicious activity. - Application Attack: are malicious activities that target software, applications, or programming code to exploit vulnerabilities and gain unauthorized access or disrupt system functionality.


