It seems that every day brings a new headline detailing a major cyberattack resulting in significant operational issues, data corruption, or data loss. T-Mobile, The US State Department, and Microsoft all made headlines for major data breaches in the last month alone!
This is due to the advanced sophistication of threat actors, increased global connectivity (IoT), and an overall lack of understanding of what is needed to effectively manage cyber risks at the executive leadership level of most companies.
It is also important to note that these headlines only capture an extremely low percentage of cyberattacks globally, and they typically don’t tell the full story when it comes to the true losses the organization may incur.
To understand the complete view, we must consider both direct and indirect impacts when assessing the overall value at risk.
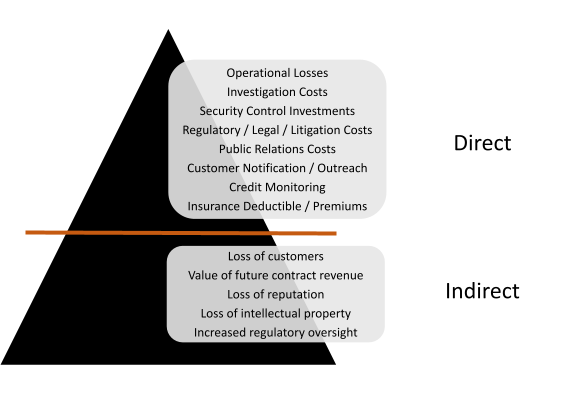
Direct Costs
During the heat of the moment, most organizations will default to fighting the fire at their doorstep. This is where the focus is turned on the costs to mitigate further immediate risks and return the business to “normal” operations. Depending on the nature of the attack (in addition to operational losses), organizations may immediately need to acquire investigative services, legal services, new technology, customer protection, and invoke insurance policies.
These are direct costs and often substantial ones.
Indirect Cost
What most organizations fail to understand is that the long-term indirect impacts can significantly exceed the direct costs required to recover from a cyberattack. The loss of future customers due to reputational harm, the ability to gain new price-competitive contracts with existing customers, and even the loss of intellectual property can hamper your organization’s ability to succeed, or even continue to operate.
Risk Multipliers
You also need to consider the factors that will exponentially increase your cyber risk profile. Data types (PII, SPI, PHI), intellectual property, jurisdiction, and overall revenue must all be considered when evaluating potential impacts. You should also factor in who is managing your data and how having multiple hosts (suppliers/partners) for your data can increase the likelihood of unauthorized exposure.
Did you know:
- The average cost of a data breach (under 100,000 records) is 3.86 million dollars (4.5 in CA, 8.6 in the US)
- The average number of days to identify and contain a cyber breach is 280 days
- Stolen credentials are the leading cause of breach 19%
- Lost business is the largest contributing loss factor 40%
- Incident Response preparedness was the highest cost-saving factor 38% ($2 million)
Data provided by ponemon.org
How We Can Help
At White Tuque, we believe the first step to protecting your assets is understanding your business and the associated risks. Using an advanced and risk-based approach that adapts to the evolving threat and regulatory landscape, White Tuque can become your trusted cybersecurity and resiliency partner.
To learn more about our services, please reach out to us to schedule a free initial consultation.

